Recent Posts
- Online Registration - Best Practices Today and Tomorrow (Monday, May 24, 2010)
- Education is now about filtering information, not finding it (Thursday, November 12, 2009)
- How Social Networking Will Affect Privacy and Data Security of Your Events (Thursday, September 10, 2009)
- Using Technology to Reduce Housing Costs at HSMAI Affordable Meetings in Washington D.C. (Wednesday, September 9, 2009)
- Twitter: I don't get it, but I'm going to give it a chance (Wednesday, August 12, 2009)
- When technology saves you time but does not help your work. (Thursday, June 11, 2009)
- Think you'll never attend a meeting in a Virtual World? Look out behind you! (Friday, May 29, 2009)
Monday, February 23, 2009
Identity theft - the most prevalent crime in America?
Enter the Secret Service
Daniel A. Baker spoke immediately before me. He's a Special Agent from the Oklahoma City Field Office of the U.S. Secret Service and he gave a fascinating talk on identity theft. I spend most of my time trying to prevent credit card and information theft, so it was interesting to see the law enforcement perspective that takes over when prevention fails.
One statistic that hit me was that 3 or 4 out of ten Americans have been victims of identity or related theft (e.g. credit card fraud) either directly or through family members. To me, that implies that identity theft is the most prevalent crime in America.
Do we spend most of our time fighting crimes people don't commit?
Another interesting statistic came in my mail from the City of Lewisville. Homeowners with registered alarm systems now must pay $50 per year, because 99% of the 6,000 residential alarms that Lewisville police respond to are false. So, last year our police spent more time responding to about 50 break-ins (and nearly 6,000 false alarms) than to the several hundred identity fraud crimes that I'd expect in a city of 100,000. As I've blogged in the past, I've had $1500 stolen (and refunded) from credit card fraud and an attempted theft of nearly $24,000 in check fraud, yet no law enforcement agency I contact has the resources to tackle such "small" crimes.
I'll keep working on fraud prevention, but I wonder if the criminals are staying a step ahead of us with these newer electronic crimes?
Wednesday, December 31, 2008
PCI Data Security Standard Version 1.2 Takes Effect
The end of Wired Equivalent Privacy (WEP) wireless security
The major practical change that I found in PCI v1.2 is that new implementations of WEP security in Wi-fi Internet access are not allowed after March 31, 2009. Current implementations must discontinue use of WEP after June 30, 2010. WEP is a popular security option for Wi-fi installations, however, it became obsolete in 2004 with the completion of the Wi-Fi Protected Access (WPA) standards, and WEP is dangerously vulnerable. Nevertheless, WEP remains the default option for wireless security with many Wi-fi routers.
If you haven't migrated your Wi-fi networks away from WEP yet (or if you are still using unsecured Wi-fi), make it one of your New Year's resolutions to update your wireless security.
Happy New Year
2008 marked my ten-year anniversary working on Certain Registration (originally Register123). I wish you all a Happy New Year and best of luck in 2009.
Thursday, September 04, 2008
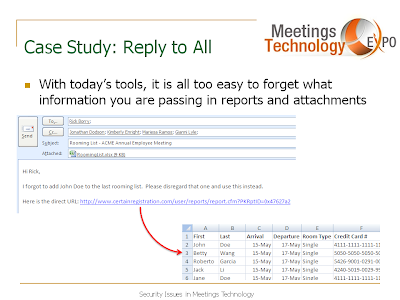
Security for Web 2.0 presentation at MTE in Washington DC.
Security for Web 2.0
Below are the slides from my presentation. Click on any image to see a larger version.

Friday, March 16, 2007
Why be PCI Compliant?
Scam 1: "Please refund my other card"
I heard this story from one of our clients during a recent Performance Analysis.
An attendee registered for a training conference and attempted to use several different credit card numbers to pay for his tuition. (He eventually completed payment with a Visa card.) Weeks later, he sent an email to the event's registration support contact explaining that he would be unable to attend the conference, but that he had recently switched credit cards and would like the refund to be posted to his new credit card number. The support contact decide not to do this, because (1) PCI Compliant systems like Certain Registration don't support this process and (2) the request, combined with the number of failed payment attempts using multiple credit card numbers, "smelled fishy".
Later, the client found out that the Visa card used for tuition payment belonged to a older woman in Arizona, and after piecing this puzzle together, they refunded the full amount to the original card. Our contact notified their corporate security department, who in turn contacted the FBI's Internet Crime Complaint Center (IC3). It turned out that the "attendee" was a Ghana national involved in a fraud operation much larger than this incident. Fortunately for our client, because they listened to their instincts instead of immediately trying to satisfy the attendee's request (and because they were using a PCI compliant system), the investigation could be turned over to the FBI without financial loss for either them or the credit card victim.
Scam 2: "Sorry, but I wrote the check for too much"
The second experience hit closer to home. I recently moved and listed my previous townhouse for rent. I received an email from "Marcus", who informed me that he was placing a colleague in the north Dallas area for a year and would like to rent the house, and would it be okay to pre-pay six months' rent in advance? My suspicion was raised by the poor grammar in his email, but you can't argue too much with cash up front, so I accepted the offer.
Two days later I received a DHL overnight package from Dubai, United Arab Emirates with a cashier's check for $35,300 drawn on JP Morgan Chase Bank in Florida. Great - except that six months rent plus deposit was only $11,200. He then sent me an email stating that he had accidentally cut the check for too large of an amount, but he was not able to change it so could I please cash the check and then wire transfer the difference ($24,100) to his bank in the UAE?
Well, that was the end of the business deal for me, but I have learned that this con is common enough to get it's own FTC warning, and successful enough that the FBI IC3 is only interested in your case if you actually lost money. A few mornings later, I received a phone call from "Marcus" (which showed on my caller ID as originating from a Dubai country code) and from the background noise activity it certainly sounded like he worked in a call center operation as busy as that of any medium-size business in the U.S.

It's a jungle out there
The Internet has brought the world together, but unfortunately much of our world is still the Wild West. Be careful out there, and follow best practices like those of the PCI Standards.
Friday, March 09, 2007
PCI Compliance Part 3 - Don't lose that credit card data!
Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need-to-know
This sounds like a page out of a classic spy novel, but the principle of "need-to-know" is a foundation of good security. Only users who specifically need access to credit card data should have access to the system that contains that data. If a user has access to other parts of the system, then by default they should not have access to unencrypted, sensitive credit card data. Lastly, administrators should grant access to cardholder information only to the minimum number of users who specifically need to see that information for a legitimate business reason that has no alternative.
In Certain Registration, for example, some meeting planners still collect credit card numbers from their attendees in order to "guarantee" their room reservation. These planners need to deliver the unencrypted credit card number to the hotel if the registrant is a "no-show" for the room, thus they have a legitimate business reason to view the full credit card number and their User access can be granted permission to see those numbers. However, all other users will only see the last four digits of the credit card number if they attempt to view the same reports.
In the near future, as more companies adopt PCI compliance, I suspect that no hotels will be willing to receive a list of unencrypted credit card numbers and will thus require room blocks to be guaranteed against the master account. Then the current "legitimate business need" to view these numbers will disappear, and such access can be ended. In this case, the planner can still store the credit card information in encrypted, unreadable format, and they can charge the registrant's card if they are a no-show without any human being able to read the cardholder data.
Requirement 8: Assign a unique ID to each person with computer access
If you are going to restrict access to data via an authentication scheme (such as username/password), then each individual person must have their own authentication. If multiple people share a single username, for example, then the system cannot audit which person made specific actions, only which username made those actions.
In order to make sure that only the intended user has access to a given username / password combination, PCI places multiple restrictions on systems:
- Passwords must be at least 7 characters long, with a combination of alphabetical and numeric characters
- Every 90 days, passwords must be changed and inactive user accounts must be removed
- The user must be authenticated prior to changing or resetting passwords, e.g. by sending a temporary password to the User's email address
- User sessions without activity for 15 minutes must be automatically timed out and require login to re-start
Some of these security requirements, such as the 15-minute timeout rule, can be annoying for users who don't need access to credit card information. Thus our system gives those users the options to adhere to a less restrictive security policy - but they cannot view credit card data. Any user who can view cardholder data must adhere to the PCI guidelines and live with its inconveniences.
Requirement 9: Restrict physical access to cardholder data
PCI requires companies to control physical access to cardholder data; this includes access to the database servers, backup media files (which are often stored offsite), paper hardcopies, etc. Modern Network Operations Centers (NOC), such as ours at NTT Verio, provide this control through 24/7 security, photo-badges with biometric hand scans, individual cages and cabinets, and constant video monitoring.
Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data
PCI requires us to log all activities related to accessing cardholder data, plus all activity related to controlling access to that data. So everytime an Administrator creates a new user with access to cardholder information, we record the action in a log. If a user runs a report with cardholder data, the action (and content of the report) is logged. These logs cannot be deleted by Administrators, and are available online for a year after the action occurred.
Requirement 11: Regularly test security systems and processes
Periodically, security vulnerabilities appear due to new techniques discovered by hackers or researchers or software updates. PCI requires adherants to monitor critical files for changes, scan internal and external network vulnerability quarterly, and perform annual detailed security tests on all systems.
In addition, networks need to have an "Intrusion Detection System" (IDS), which is basically an observation post that watches the data traffic flowing through your network and looks for patterns that indicate malicious data attacks or a security compromise.
Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security
Companies that collect cardholder information must publish written security policies that adhere to PCI compliance. The policy should be known by all employees and contractors, and any outside vendors who receive cardholder information must also be PCI compliant.
Since most data security breeches are caused by internal behavior, all employees who have access to credit card information in bulk format must be screened prior to hiring. For example, we perform credit checks and criminal checks on employees as part of the hiring process.
Saturday, February 24, 2007
PCI Compliance Part 2 - Don't lose that credit card data!
Below are the 12 major requirements of PCI Compliance, described in layman's terms.
Build and Maintain a Secure Network
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
A firewall is an electronic barrier between the outside world (which is dirty) and your data (which is hopefully clean). Computers and servers are like houses with thousands of windows, called "ports". Data can flow in and out of these ports, for example, web browsers typically use port 80 for "http" requests and port 443 for "https" requests. A firewall is like a window shutter - it provides a barrier to traffic flow on the ports that you don't need to use.
Sophisticated firewalls can even close ports to specific types of data and can provide "dual-zone" protection. A dual zone firewall means that you can have one set of protection for your web servers (which must have ports 80 and 443 open to the world in order to deliver web pages) and a second set of more restrictive protection for database servers (which only need to communicate with the web servers and thus can be closed to the rest of the world). The more ports you close or restrict, the tougher it is for bad guys to get in.
It's like the battle for Helm's Deep in Lord of the Rings - Twin Towers. If the orcs get through the outer defenses, then they still have to breach the walls of the keep in order to get to your people. Yeah - it's exactly like that…
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters
This requirement is so obvious that it is painful to write, but a surprising number of web servers use blank or system default passwords for their administrator access. Just ask my neighbor, who purchased a Linksys WI-FI router last year and still doesn't know that I get better access on his network from my laundry room than I do on my own network. (Actually, please don't tell my neighbor.)
Protect Cardholder Data
Requirement 3: Protect stored cardholder data
This requirement is really two parts:
- You can't store certain types of cardholder data at all, e.g. the CVV/CV2 number or PIN or magnetic stripe contents. You can only use that data one time for authentication, and then must remove the data from memory.
- Any data that you do store (Cardholder name, card number, expiration date, bank information) must be protected.
The PCI standard requires the your encryption key, the code which unlocks the encrypted value, to be stored only in temporary memory. That means that we have to enter the code phrase every time we reboot our servers, and there is nowhere on the physical drives that someone could read this key and decrypt the stored credit card numbers. Furthermore, registrants and administrators only see the last 4 digits of the credit card number on their screen (e.g. ******1111) and even the encrypted card information is deleted 90 days after the event ends.
Requirement 4: Encrypt transmission of cardholder data across open, public networks
Most internet users know the difference between "http" pages, which are transmitted in plain text across the Internet from your browser to the server, and "https" pages, which are encrypted by your browser prior to transmission to the server. Whenever we deal with credit card data, we use an "https" connection. This way if someone were to tap into your data lines and read the information passing between your computer and a web server (which is surprisingly easy to do), then they couldn't get any meaningful information.
Secure connections ("https") require the web site to have a secure certificate, which must be renewed periodically. For example, ours comes from Entrust:

Maintain a Vulnerability Management Program
Requirement 5: Use and regularly update anti-virus software
PCI requires companies to have anti-virus software on all servers and personal computers that collect, store, or transmit cardholder data. Modern anti-virus software is continually updated to protect against new viruses, and it scans the computer's files and data traffic for viruses, spyware, adware, and other undesirable programs that might be trying to collect credit card information for a malicious user.
Requirement 6: Develop and maintain secure systems and applications
Requirement 6 means that software vendors must follow processes that maintain their application at the highest level of security, for example:
- Apply all security patches from software companies within 1 month of release
- Subscribe to alert services for newly-discovered vulnerabilities
- Separate development, test, and production environments
- Develop applications within the best practices of the Open Web Security Project
- Have an outside application security firm review code for common wulnerabilities
Tuesday, February 13, 2007
PCI, FACTA, CISP, SDP - Just don't lose those credit card numbers!
Lost yet? Well, it turns out that the politicians and various credit card companies each tackled the problem of credit card security separately.
Payment Card Industry Data Security Standards
PCI stands for Payment Card Industry - an association that reflects the combined interests of VISA, MasterCard, Discover, American Express, and JCB to promote financial data security standards. Prior to publication of the PCI Data Security Standards in September 2006, each card brand managed their own set of requirements. I first implemented VISA's Cardholder Information Security Program (CISP) in 2001, and Certain had maintained compliance with it ever since. We were about to embark on MasterCard's program (Site Data Protection or SDP) when the PCI Standard was announced, which obviously saved a lot of time and money for online vendors who accept multiple credit card types.
We fall into the "Level 2" category for PCI Compliance, for processors with between 150,000 and six million annual transactions. Nevertheless, we plan to grow and want to be as secure as practical, so we opted to achieve Level 1 compliance.
There are six categories of PCI compliance security standards, with 12 broad requirements. I'll cover these details another day, but if you want to read ahead there's always the PCI Compliance Guide.
FACTA and Your Taxpayer Dollars at Work
While the five major credit card brands were solving the problem of data security in a way that made business's lives easier, in 2003 Congress passed the Fair and Accurate Credit Transactions Act (FACTA), an amendment to the Fair Credit Reporting Act (FCRA).
Section 113 of FACTA (don't follow that link!) took effect in December 2006, three years after the amendment was passed into law.
SEC. 113. TRUNCATION OF CREDIT CARD AND DEBIT CARD ACCOUNT NUMBERS.
Section 605 of the Fair Credit Reporting Act (15 U.S.C. 1681c) is amended by adding at the end the following:
(g) Truncation of Credit Card and Debit Card Numbers.--
(1) In general.--Except as otherwise provided in this subsection, no person that accepts credit cards or debit cards for the transaction of business shall print more than the last 5 digits of the card number or the expiration date upon any receipt provided to the cardholder at the point of the sale or transaction.
However, page 6 of the PCI DSS self-assessment questionnaire says nothing about expiration dates, but it does ask, "Are all but the last four digits of the account number masked when displaying cardholder data?"
I guess Congress thinks they know more than the businesses whose livelihoods depend on the security of cardholder data, but anyway, after our patch this week the transaction on Certain's confirmation page will change from
Richard Borry (Visa ******1266 exp. 10/08)
to
Richard Borry (Visa exp. 10/08)
and as a result we will be compliant with FACTA, PCI, CISP, and SDP.
The Bottom Line
Enough with the acronyms and anti-government over-regulation diatribe. What I hope you learn is that:
- Professional web software providers care deeply about the security of your credit card data
- Companies like Certain spend hundreds of thousands of dollars to adhere to the state-of-the-art standards, and to maintain compliance to those standards as they change
- You do *not* want to deal with this yourself
Ask your software vendor about PCI Compliance, ask to see an independent audit report, and think twice when your IT group says "No problem" about building an in-house system that will handle credit card data online.